Key takeaways
- Workplace privacy laws are a set of enforceable guidelines that protect employee privacy from employer misuse.
- Federal law allows employers to monitor emails and messages, computers and laptops, phone calls, and locations.
- Privacy by Design can help you design a secure workplace with privacy protections installed.

When it comes to commercial security awareness in the workplace, there are many things to consider regarding employees’ privacy. For instance, how do you protect their data and sense of privacy in a high-control security setting? How do you adhere to workplace privacy laws while maintaining safety through strict security monitoring?
In this post, you will discover what privacy laws cover in the workplace. Then, you’ll learn how to abide by the law while keeping your employees and workplace safe. Last, we give you a rundown of what you can monitor within your company’s workplace.
In this post:
- What are workplace privacy laws?
- What you can monitor in the workplace
- Introducing Privacy by Design
- FAQs about privacy laws in the workplace
What are workplace privacy laws?
Workplace privacy laws are a set of enforceable guidelines that protect employee privacy from employer misuse. These guidelines don’t assume employers will intentionally risk employee privacy, but they give people actionable boundaries.
These laws on privacy in the workplace expressly protect an employee’s right to privacy concerning:
- Personal information. The Privacy Act of 1974 establishes the employee’s right to personal information. As such, employers cannot share personal information about the employee with others inside the organization or with third-party agencies under most circumstances.
- Medical information. Most commonly known as HIPAA, this privacy act protects employees’ medical information from being released without their permission.
- Background checks. The Fair Credit Reporting Act requires employers to obtain permission from prospective employees to conduct background checks.
What you can monitor in the workplace
According to federal law, these are the things you can monitor in the workplace:
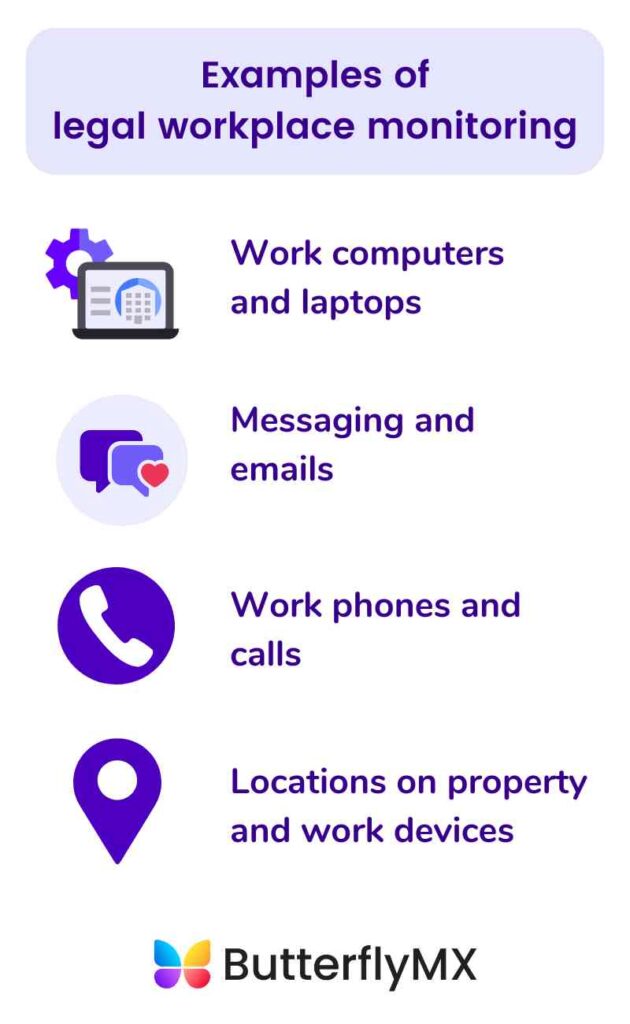
Emails and messages
Workplaces can monitor emails and messages on work channels within reason. As such, employees should use caution when using work emails for private messages. Moreover, monitoring emails means that scams and phishing emails are easy to neutralize.
What’s more, employers can monitor messages between employees on work channels.
Computers and laptops
Work computers and laptops that a company provides are within reasonable monitoring range. Companies usually set up an app or service on computers lent to their employees.
As such, these applications run scans on computers to check for viruses and ensure computers aren’t used in ways that violate company guidelines.
Work phones and calls
What’s more, phone calls made on company phones are subject to monitoring, especially in sales settings. Many employers keep tabs on work calls for their own protection and their employees’ protection.
In most cases, these calls are only monitored when they occur on workplace property or on a work-designated phone.
Locations on work devices
Many companies give employees a phone, laptop, or—in some cases—a vehicle. As such, the location services on these devices are subject to workplace surveillance.
While some might argue about the ethics of this type of workplace monitoring, it’s still allowed in most cases unless settled otherwise.
Likewise, security cameras on premises are permitted to surveil visitors and residents as they come and go from the building and move within the location.
Discover office automation technology:
Introducing Privacy by Design
It can be difficult to manage a compliant workplace security system that protects employee information while also securing the organization. That’s where Privacy by Design comes in.
PbD means that privacy is the default in all of an organization’s security protocols. As such, the protection of data is embedded in any system and shouldn’t be changed to suit a company’s needs over that of the employee.
What are the principles of Privacy by Design?
The principles of Privacy by Design are:
- Proactive, not reactive. It’s advised to proactively anticipate data breaches instead of reacting to them as they happen. This will help protect your employees’ data from the start.
- Privacy as default.
- Any new workplace security system design, IT service, or visitor management system should always prioritize privacy. Your organization should strive to minimize data collection as much as feasible.
- Privacy embedded. Your organization holds the responsibility of protecting the privacy of employees and customers. Thus, it’s your job to ensure that all systems, services, and applications have privacy protection embedded before using them.
- Full functionality. If you want to use a service or security system’s full functionality, you must ensure that privacy protections are firmly established at all levels of use.
- End-to-end security. End-to-end security means that protections during workplace monitoring are in place during the entire lifecycle of the process.
- Visibility and transparency. If your company engages in data practices, you’re obligated to be transparent about it and inform everyone involved.
- Respect for privacy. Lastly, no matter the size of your organization, respect for user privacy should be at the heart of your data and security practices.
FAQs about privacy laws in the workplace
Here are answers to common questions about privacy laws in the workplace:
- What is considered an invasion of privacy in the workplace?
- What is the federal law for employee privacy?
What is considered an invasion of privacy in the workplace?
When an employee feels their private information is being used or shared without a lawful reason, it’s considered an invasion of privacy in the workplace.
This can include sharing personal information with coworkers, a third-party agency, or a social network.
What is the federal law for employee privacy?
Officially, the federal law regarding employee privacy is The Privacy Act of 1974. This act covers the collection, maintenance, and sharing of personal information regarding employees.