Key takeaways
- Security technology is the tools and methods that enable physical and cyber security at your property.
- The four elements of security technology are prevention, deterrence, detection, and response.
- The top security technology trends dominating real estate are security system integration, mobile-based management, remote access control, and merged video surveillance and access control.

Since the dawn of the real estate industry in the late 1800s, property security has been a valuable commodity. And traditional physical security measures like guards, gates, and locks are still widely used. However, modern security technology incorporates software, transforming security into a well-rounded, robust system.
In this guide, we define security technology and its main elements. Then, we outline the most common types of security technology. Finally, we cover the top four security technology trends dominating the industry.
This post covers:
- What is security technology?
- What are examples of security technology?
- 6 security technology trends dominating the industry
- The best security technology to buy
What is security technology?
Security technology is the tools and methods that implement security protocols in buildings. In other words, security technology enables physical security, cybersecurity, and AI security at your property.
A robust security system is more than just its individual parts, however. Security technologies must consist of several components that work together to create a well-rounded security system.
Four elements of security technology:
- Prevention. This is your best approach to property security. This includes cyber security technologies designed to slow or deter intrusions, such as two-factor authentication or data encryption.
- Deterrence. Keep would-be intruders away. For example, an intercom with a camera will deter burglars. Additionally, installing IoT-enabled door locks and multiple access points will discourage trespassing.
- Detection. Quickly identifying security breaches can be the difference between small damages and detrimental ones. In any case, software that notifies you when doors are forced open or set off alarms is essential.
- Response. No matter what precautions you take, a building is never completely safe from security breaches. Having a quick response time to breaches protects you from significant damage.
What are examples of security technology?
Security technology consists of two categories: physical security and cyber security.
There are several differences between the two. However, security strategies that incorporate both and empower them to work together are best.
Physical security
Physical security protects property from physical intrusions, typically intruders and thieves. However, the fallout from natural disasters like hurricanes and hail storms can also be prevented with physical security.
Three components of physical security:
- Access control
- Surveillance
- Testing
Because all three of these aspects are equally important — and can’t function without one another — you must ensure your property’s security system pays equal attention to all three.
For example, surveillance is great, but without access control measures in place, people can easily get into restricted areas. Additionally, your surveillance and access control measures may work well in tandem. But without routine testing, any issues will go undetected until a breach.
Types of physical security:
- Perimeter security, examples of which include gates, garage doors, and fences.
- Access control such as fob systems, smartphone-based intercoms, and locks and keys.
- Surveillance systems that spot intrusions, like cameras, fire alarms, and motion detectors.

Cyber security
Being able to connect all smart devices is convenient, but it does leave you vulnerable to hackers. To combat this, you must employ cybersecurity tactics.
Cyber security protects everything that physical security can’t. Further, when used in property management, cyber security protects information for you and your tenants.
Information protected by cyber security includes:
- Credit card and payment information
- Passwords to resident portals
- PIN codes for keypads
- Resident identification data
In order to effectively implement cyber security technology, you must develop a plan that includes every type of cyber security.
There are five distinct types of emerging cyber security technologies:
- Application security refers to barriers coded into an application during creation, such as data encryption and end-to-end encryption. Moreover, protecting cloud, mobile, and web-based applications from vulnerabilities prevents hackers from modifying or tampering with software.
- Network security includes activities and controls made to protect your networking infrastructure. To put it another way, network security ensures your underlying network infrastructure works securely.
- Cloud security refers to the policies and processes used to reduce the security risks of cloud computing. Cloud-based technology operates on a shared responsibility model. As a result, you must implement solutions to secure the cloud. These include identity and access management, as well as multi-factor authentication.
- Internet security technology protects from internet-born threats, which are behind most data breaches. In fact, online hacking is among the top actions during all stages of breaches. So, implementing email security against phishing and URL filtering that blocks risky websites will protect you from internet threats.
- Endpoint security examines files as they enter your network. This helps you spot vulnerabilities early by alerting you of unauthorized logins, viruses, and malware.
Watch and learn about the top 5 smart apartment gadgets:
6 security technology trends dominating the industry
As technology advances, so do security threats and vulnerabilities. As a result, security technology is always evolving to become smarter, more secure, and better connected. This way, security information technology is prepared to take on new challenges as they arise.
Here are six security technology trends that are dominating the real estate market:
- Security system integration
- Mobile-based management
- Remote access control
- Merging video surveillance and access control
- AI technology
- Hybrid and remote office work
1. Security system integration
Security system integration is the process of connecting all the security systems throughout your property. With security system integration, you can manage everything from a single, central hub. This way, you maximize security without being overwhelmed by multiple systems.
Not only does security system integration connect security systems, but it also connects property technology devices like sensors, smart thermostats, access control systems, and more. Once these are integrated, the property staff can manage every building process from one place.
Here are systems that can be connected by security system integration:
- Smart thermostats
- Smart locks
- Keypads
- Intercoms
- Elevator controls
- Smart appliances
- Security cameras/CCTV
- Motion sensors
- Alarms
- HVAC
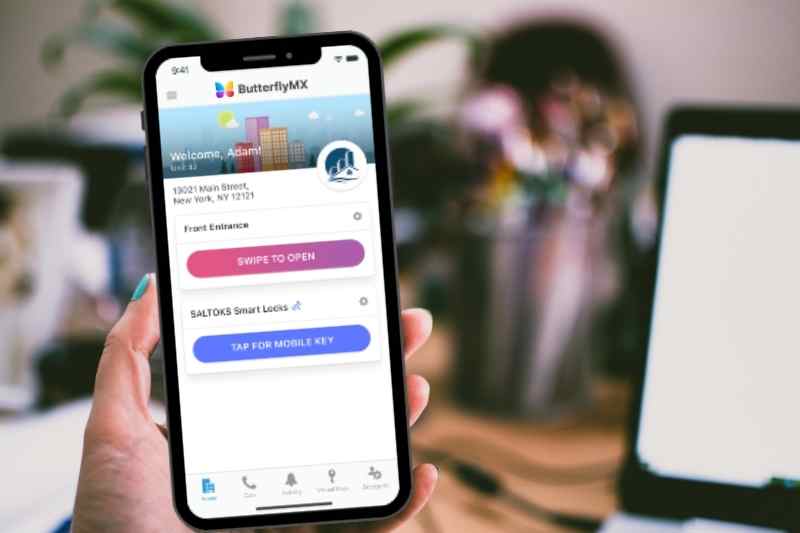
2. Mobile-based management
Your tenants do everything on their phones, from connecting with loved ones to paying bills. As mobile solutions become the norm, offering mobile-based property management is key.
Innovations like keyless door entry and swipe-to-open have transformed smartphone-based access control.
Additionally, mobile-based management means property staff can monitor access logs and surveillance at any time from anywhere. This allows you to respond to security incidents quickly, with a mobile audit trail at your fingertips.
3. Remote access control
Speaking of accessing information at any time from anywhere, remote access control is no longer a luxury, but a necessity.
Your tenants — both residential and commercial — spent a better part of the last fewyears working from home. As a result, they’ve become accustomed to walking their dogs, accepting deliveries, and greeting visitors at all times.
Luckily, you can provide the luxury of being at home by providing remote management.
It’s possible to manage lighting and HVAC systems, track and manage deliveries, and grant access to guests from anywhere.
Furthermore, remote access control makes your job as a property manager easier. Gone are the days of coming onsite for every issue. Instead, you can troubleshoot problems — and solve most access-related issues — from your phone!
Learn why WSS Integrated Technologies chooses ButterflyMX for its clients:
4. Merging video surveillance and access control
As access control solutions grow and evolve, traditional video surveillance is only growing with it. To keep up, you may consider purchasing a separate video camera to connect to existing access control hardware. However, choosing access control products equipped with cameras is a more secure and robust option.
By choosing access control products equipped with cameras, you easily integrate video surveillance and access control. This gives you a more well-rounded and complete look at door activity at any given time. Additionally, a robust system is more cost-effective and requires less work than pairing separate cameras and access control devices.
5. AI technology
Artificial intelligence is revolutionizing security technology by changing the way security devices respond to stimuli. AI-powered systems can analyze vast amounts of data in real time, swiftly detecting anomalies and potential threats that might evade traditional methods. For example, AI-powered cameras can detect human beings in the frame and, in some cases, can tell the difference between intruders and residents.
Machine learning algorithms can adapt and learn from patterns, continuously improving their ability to identify and respond to security risks. From facial recognition for access control to predictive analytics for preemptive threat detection, AI is reshaping the landscape of security by enhancing both proactive prevention and rapid response capabilities.
6. Hybrid and remote office work
Hybrid office work is becoming more popular and it necessitates a need for unique physical and digital security measures.
With employees accessing sensitive data from various locations, robust cybersecurity protocols are essential. This includes encrypted communication channels, secure VPNs, and multifactor authentication to safeguard data during transmission and access.
Physical security measures ensure that office spaces remain protected when vacant, and that they also allow employees to come and go independently without someone having to be physically present to let them onto the premises.
The best security technology to buy
The ButterflyMX suite of access control products offers some of the best security technology to buy for multifamily and commercial properties. ButterflyMX is currently installed in over 10,000 buildings and has over 20,000 five-star reviews.
Our ButterflyMX products incorporate all of the major security tech trends listed above including mobile-based management, integration with other security systems, remote access control, and video communications and surveillance.
ButterflyMX products include:
- Vehicle Reader. Our Vehicle Reader scans RFID-enabled windshield tags and grants entry to parking facilities on your property, ensuring that only verified users have access to this space.
- Elevator Controls. Restrict access to certain floors on your property so that unverified users don’t access spaces where they don’t belong.
- Package Room. Create a secure package room accessible via the ButterflyMX Keypad to ensure that packages are delivered and stored in a safe space until they can be retrieved.
- Video Intercom. Enjoy face-to-face communication with visitors, allowing tenants to verify who their guests are before allowing them onto the property.
- Keypad. Our Keypad allows users to enter via their mobile device or through a unique PIN code. Visitors can also be assigned temporary PIN codes.
- Card Reader/Fob Reader. Alternatively from using a keypad, users can utilize physical credentials such as key card and key fobs to enter secure spaces in your building.
- Front Desk Station. Manage access permissions to your property, speak directly to tenants and guests through the intercom, and monitor live video all from your mobile device.